Feds: Cardinals Guy Hacked The Astros By Using An Old Password [Updated]

Charges against former Cardinals scouting director Christopher Correa were unsealed today in federal court in Houston, finally outlining exactly how the best hacking in baseball happened, at least according to the feds. The information document was filed Dec. 22 but remained under seal until this afternoon, when Correa had his initial appearance. It outlines what prosecutors say happened in the Cardinals-Astros hacking scandal; all the details that follow are from the court documents unsealed today:
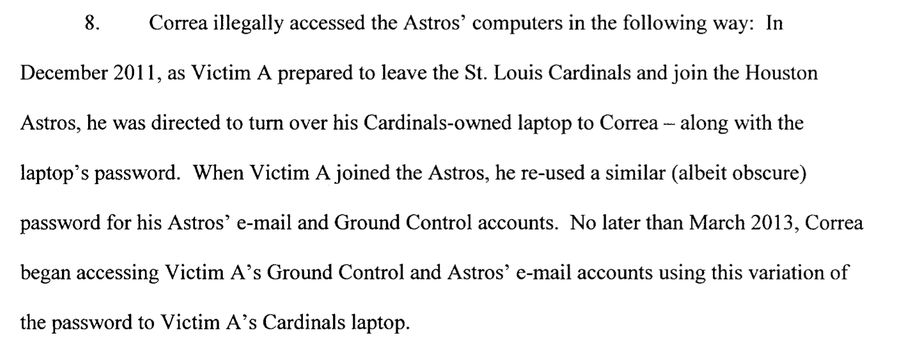
First, this all started because Victim A—presumably Jeffrey Luhnow, the Cardinals’ former vice-president for scouting and player development—didn’t change his password.
On March 24, 2013, Correa accessed Victim A’s Ground Control account and downloaded an Excel file of the team’s scouting list “of every single player eligible for that year’s draft and how the Astros ranked them.” He also viewed a variety of other internal reports, including weekly scouting digests, crosschecking reports, proposed bonuses for potential draftees, notes on the Astros, and a file kept on trade discussions.
Further, the snooping kept going. Correa accessed the Astros’ system on June 8—before day three of the amateur draft—and the pages he looked at included “information on Players I, J, and K, three players whom the Cardinals had drafted the day before.” On July 31, he logged in and used the Astros’ notes on trade discussions with other teams.
After the Houston Chronicle did a story about Ground Control, the Astros reset everyone’s passwords. Correa got around that by accessing Victim A’s email account, without authorization, and “he found the emails that contained Ground Controls new URL and the newly reset password.”

Correa is charged with five counts of unauthorized access to a computer, one count for each day listed in the charging document. He had his initial appearance today before a judge—it lasted about eight minutes—where he got a bond set at $20,000. According to the court records, Correa has already met that bond and was set to be released. He later pleaded guilty.
The full information filed today is below.
Update (3:26 p.m.): The U.S. Attorney’s Office in Houston sent out their news release about the charges, and it had a few new details about what happened. According to the news release, Correa got one ex-Astros’ employee’s password because: “When he left the Cardinals organization, the employee had to turn over his Cardinals-owned laptop to Correa—along with the laptop’s password.”
More from the press release:
The parties agreed that Correa masked his identity, his location and the type of device that he used, and that the total intended loss for all of the intrusions is approximately $1.7 million.
Each conviction of unauthorized access of a protected computer carries a maximum possible sentence of five years in federal prison and a possible $250,000 fine.
Update (3:37 p.m.): Houston Chronicle reporter David Barron was tweeting from the hearing. He reported that Correa entered a plea of guilty and admitted to finding Cardinals information. Correa said he did it, Barron reported, because he suspected the Astros had unauthorized Cardinals data. Here’s a recap.
Update (4:00 p.m.): Here’s the plea agreement, as provided by prosecutors. It mostly recaps what was in the unsealed information today and goes over more details of his punishment.
Update (5:35 p.m.): Major League Baseball issued a statement.
Deadspin staff writer Kevin Draper contributed to this report.
Image via Associated Press
Why Kansas City Chiefs Aren't Done Yet Despite 6-6 Record
NBA Best Bets Today: Sunday Dec. 7th Top NBA Picks
- College Football Conference Championship Best Betting Picks, Predictions
- UFC 323 Betting Picks: Best Bets for the Final ESPN Pay-Per-View
- NBA Best Bets Today: Top Betting Predictions for Friday Dec. 5th
- Washington Capitals vs. Anaheim Ducks December 5th Betting Picks, Predictions
- College Basketball Weekend Bets: Gonzaga, Duke, and Michigan State Predictions
- Cowboys vs Lions Thursday Night Football Betting Prediction: Week 14 Bet Picks
- NBA December 3rd Picks & Predictions: Wednesday Best Bets












